# Update existing IAM policy in AWS
Keeping IAM policies up to date ensures that organizations can effectively leverage new AWS services and features, maintaining a secure and efficient cloud environment while embracing technological advancements.
# Update existing IAM policy
Go to AWS Management Console and sign in with your account.
In the top left corner, you will see services icon. Click on it, and from the options, click on the IAM option..
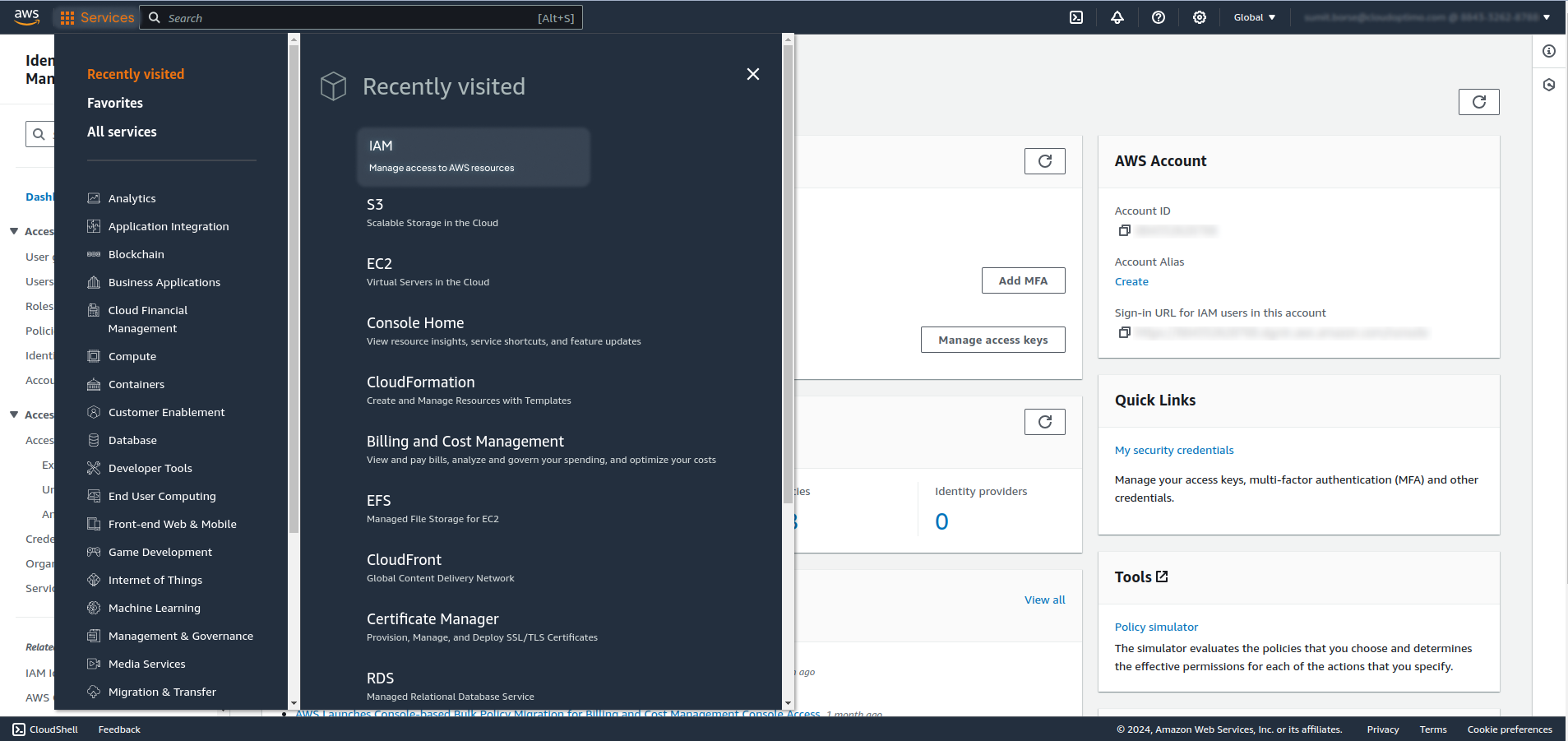
On the IAM Dashboard page, click on the Roles option from the left panel.
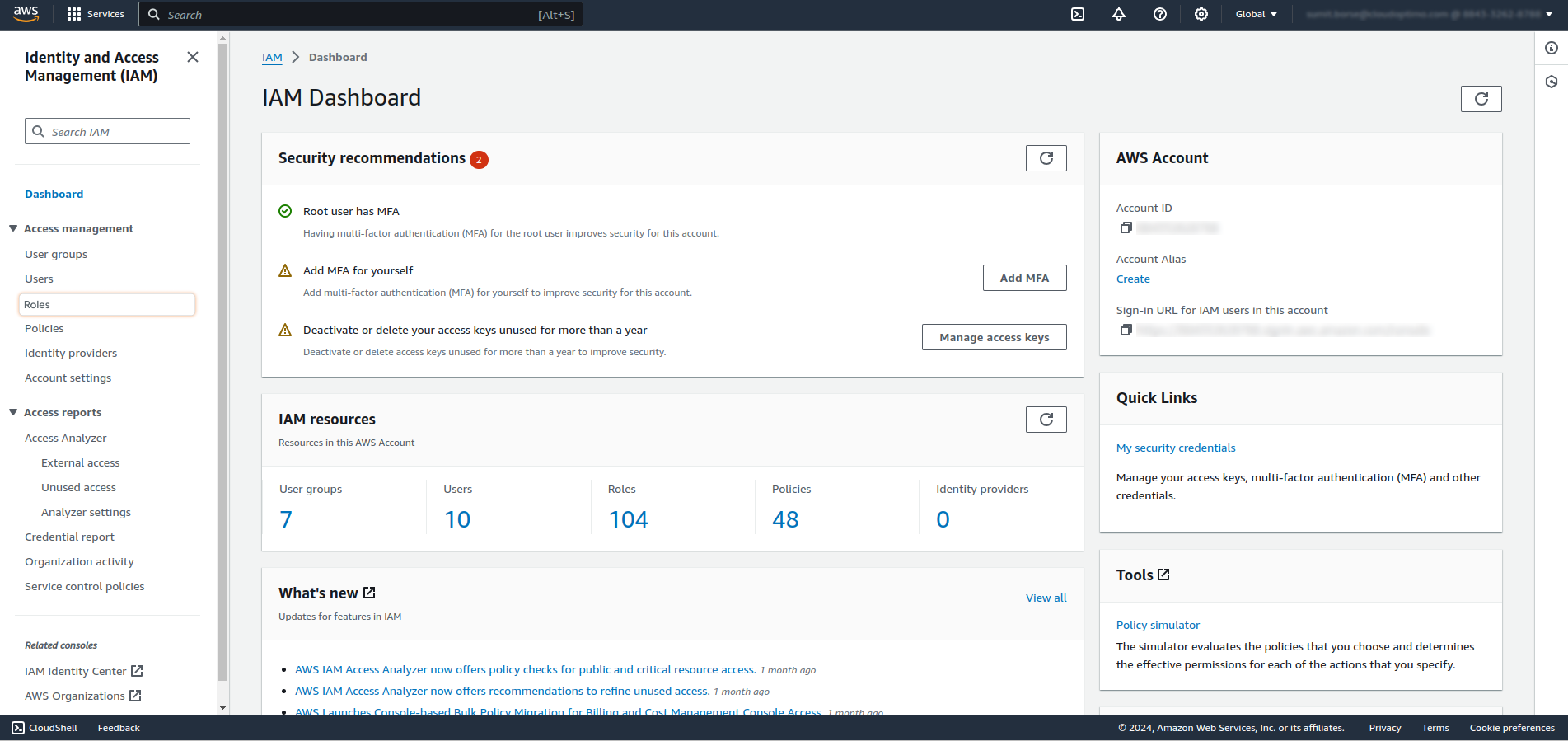
- In Search bar, enter your CloudOptimo specific IAM role name and click on that Role name.
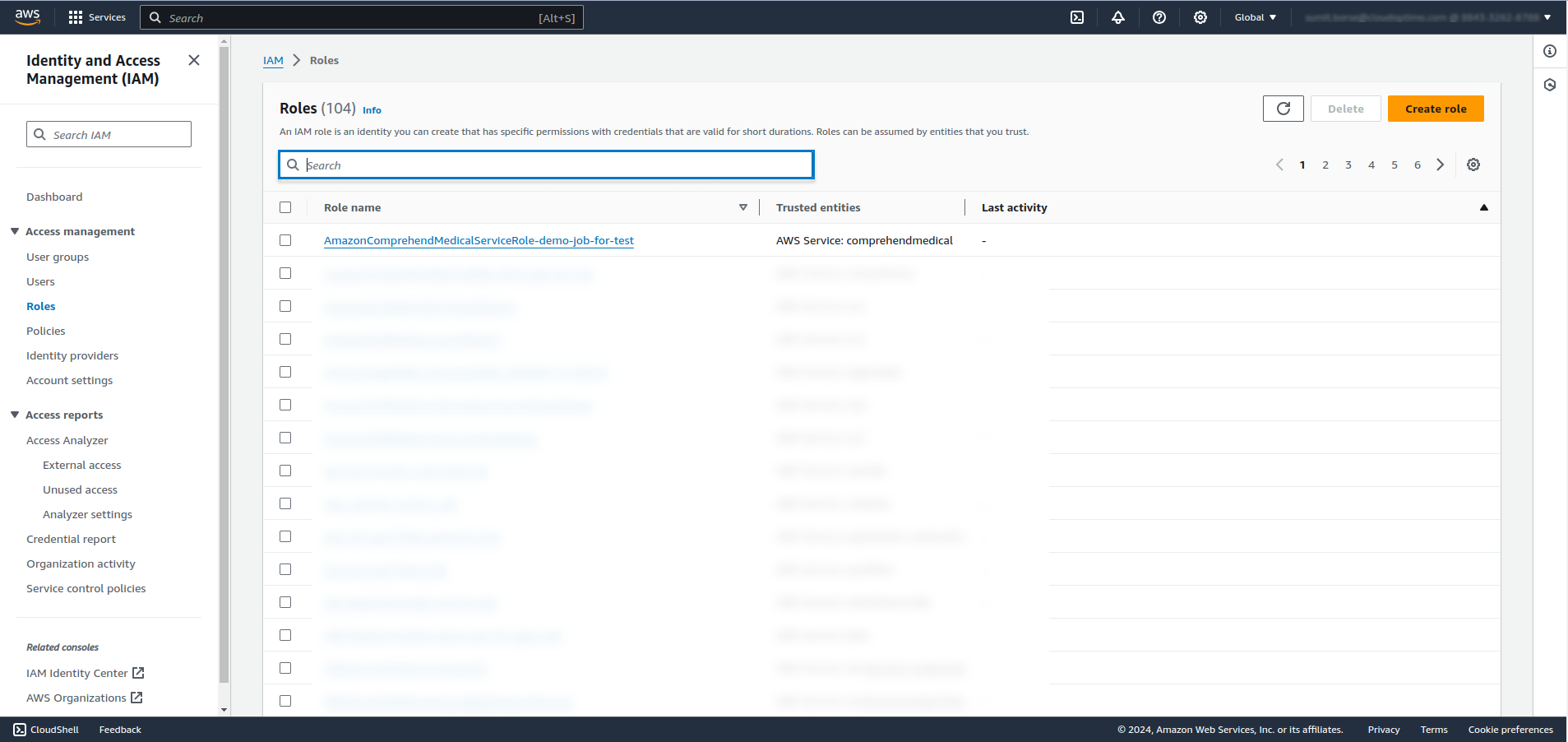
- After clicking Role name, the Role summary section opens as shown below.
- Permission Policies - Click on the Policy.
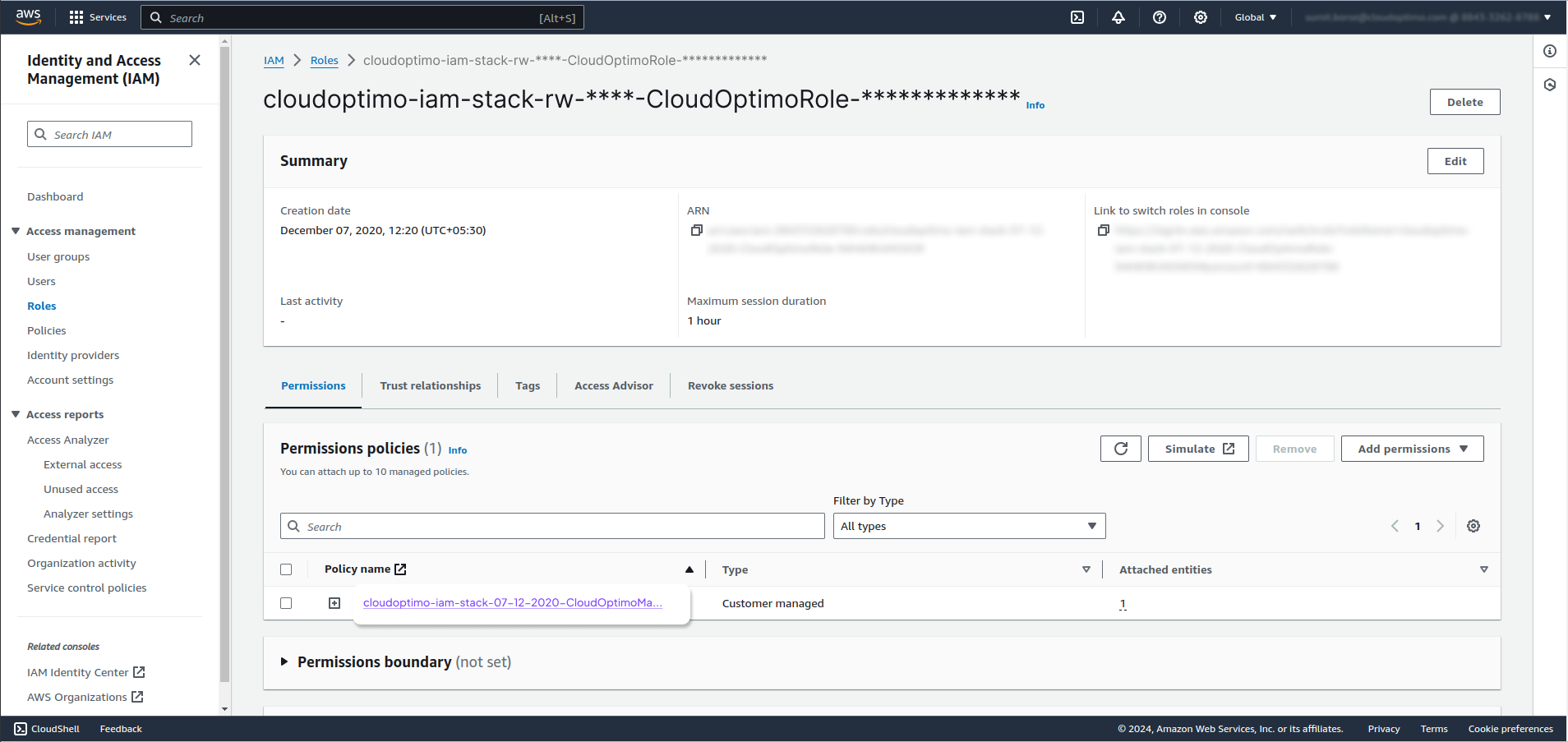
- On policy summary page , you will see the edit button at top right corner beside delete button. Click on the Edit button.
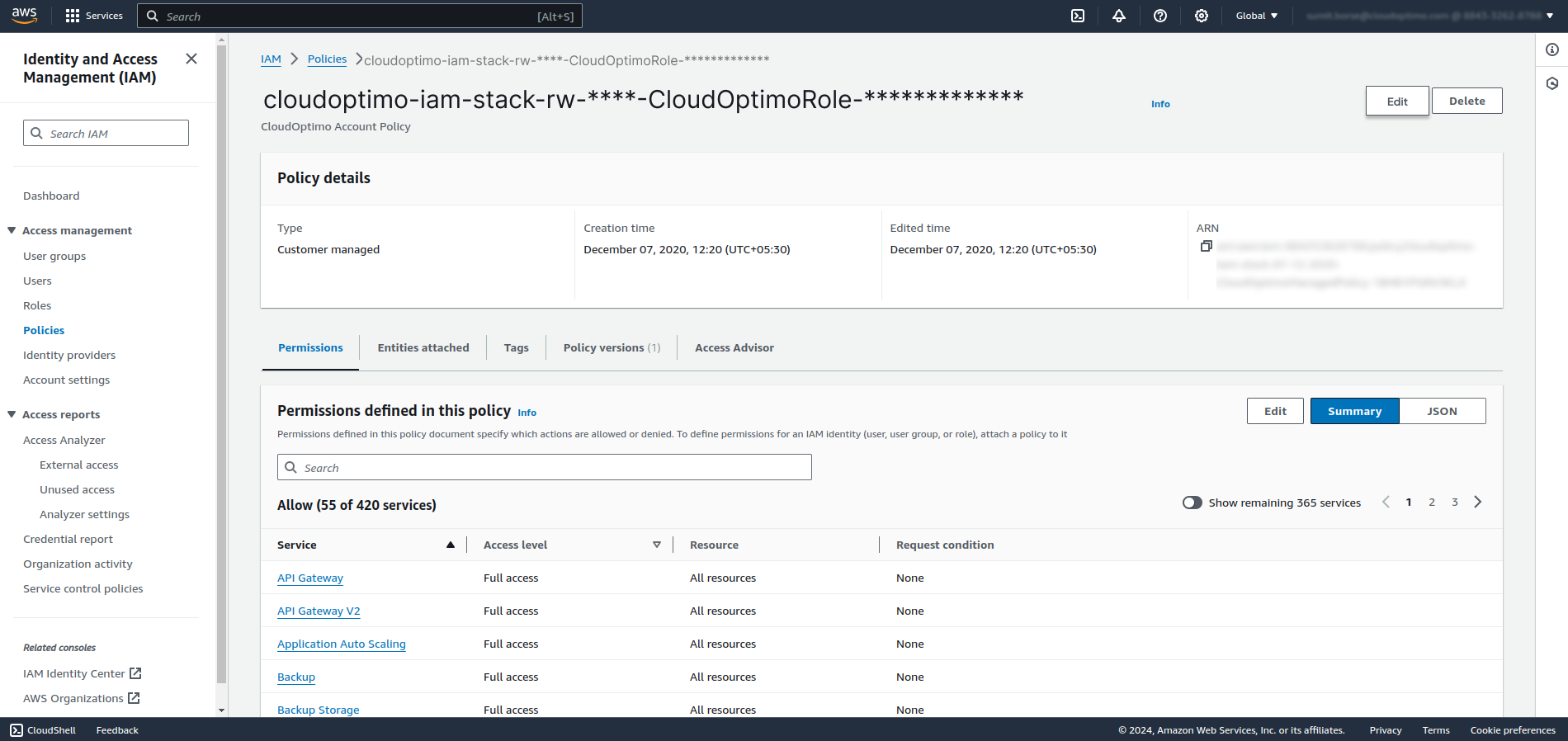
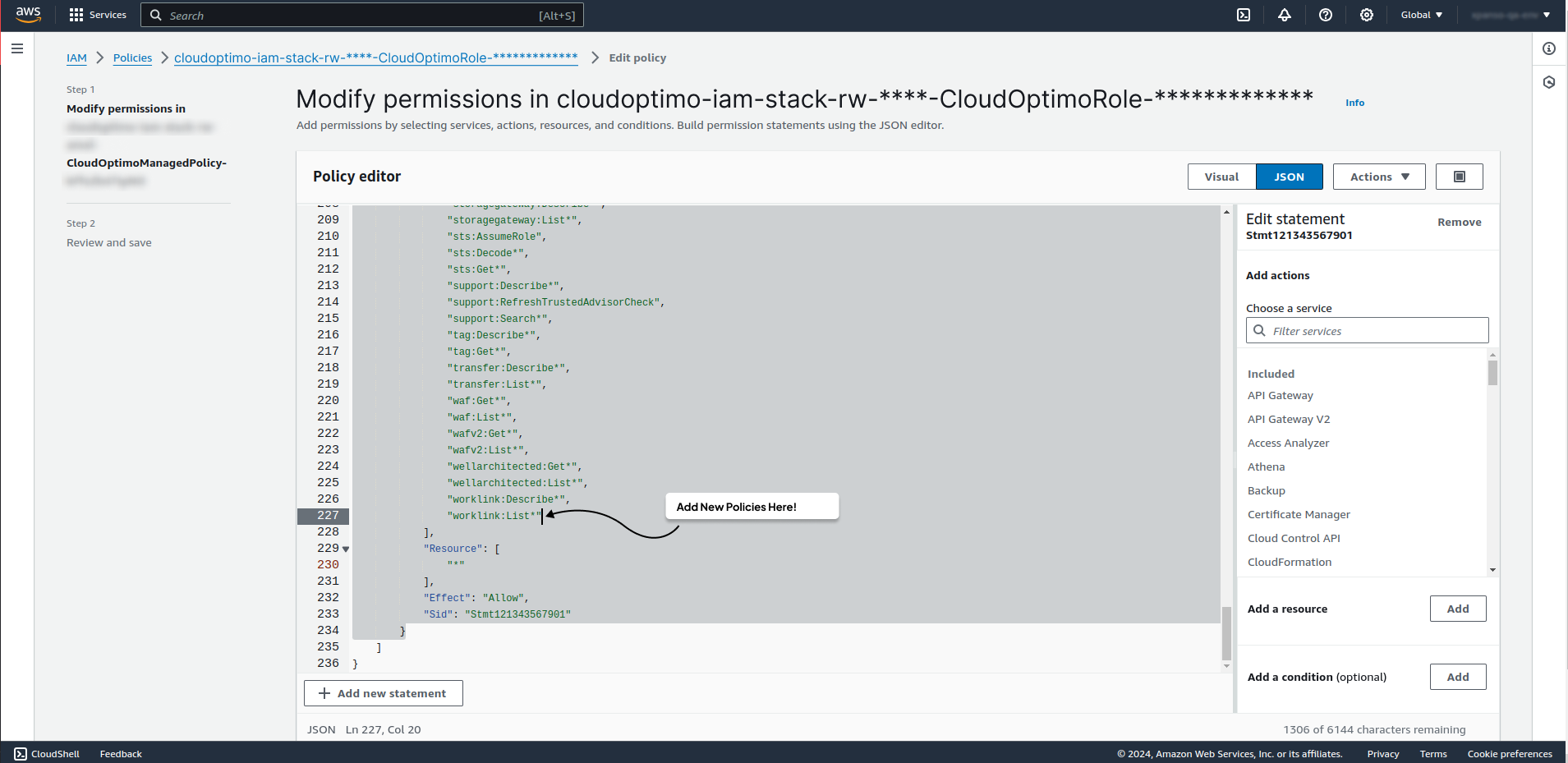
- The Policy editor window opens as shown below. Now you can add the new policies here.
- After adding a new policies scroll down on same page.
- After adding new policies, the existing JSON looks like the following
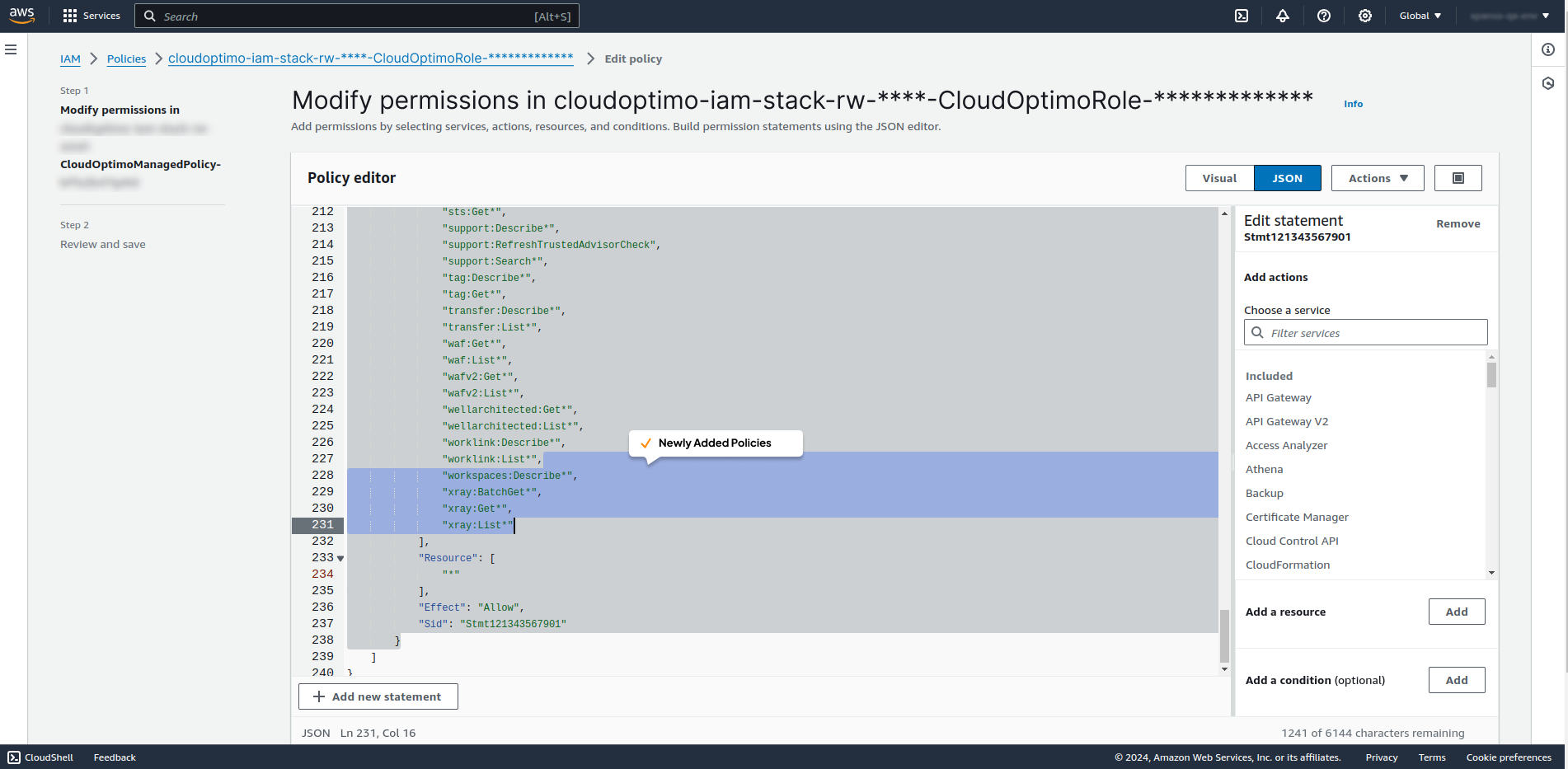
- Click on Next button.
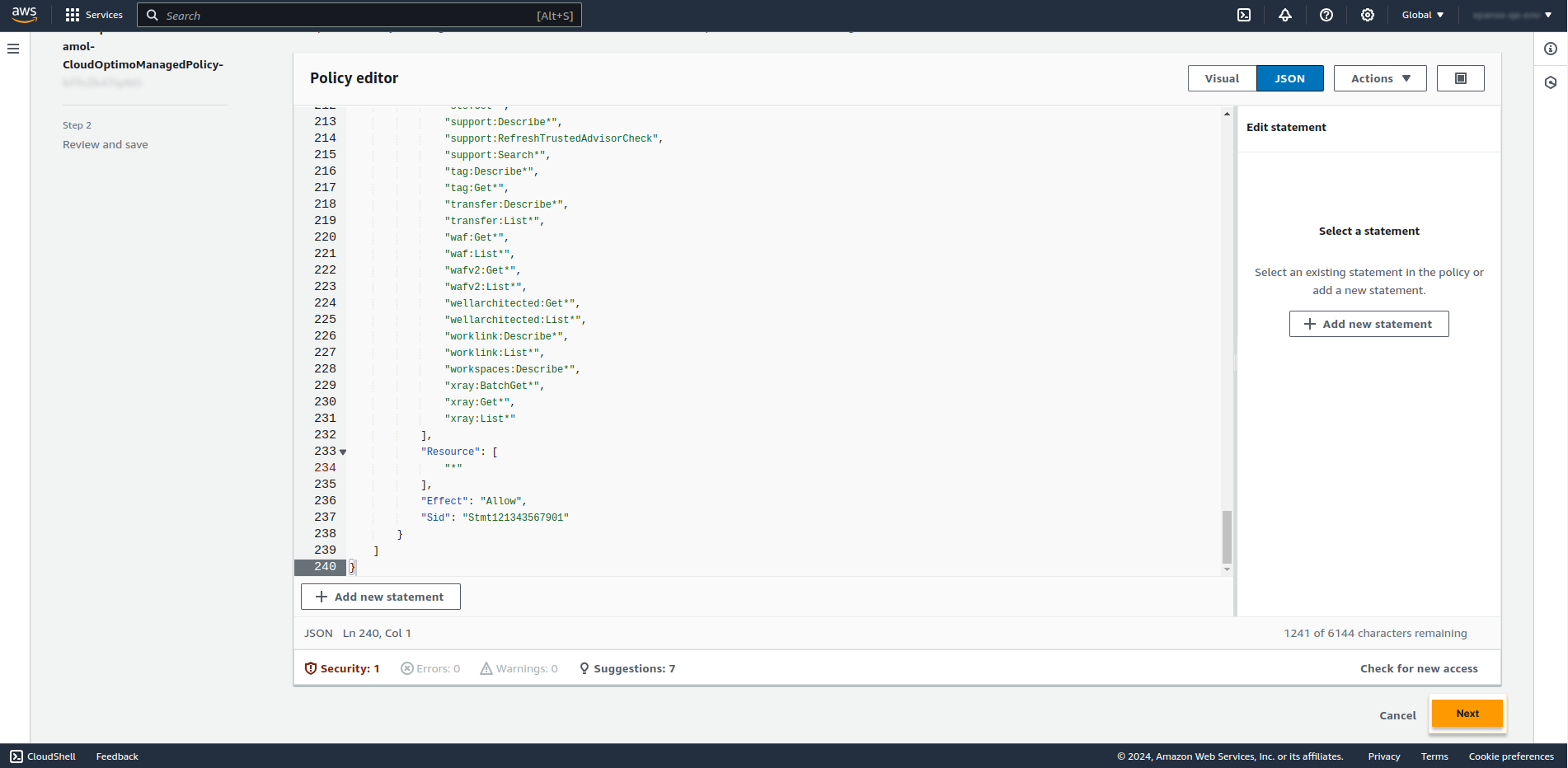
- Now you will see the Review and Save page as below. Review all policies and scroll down on same page.
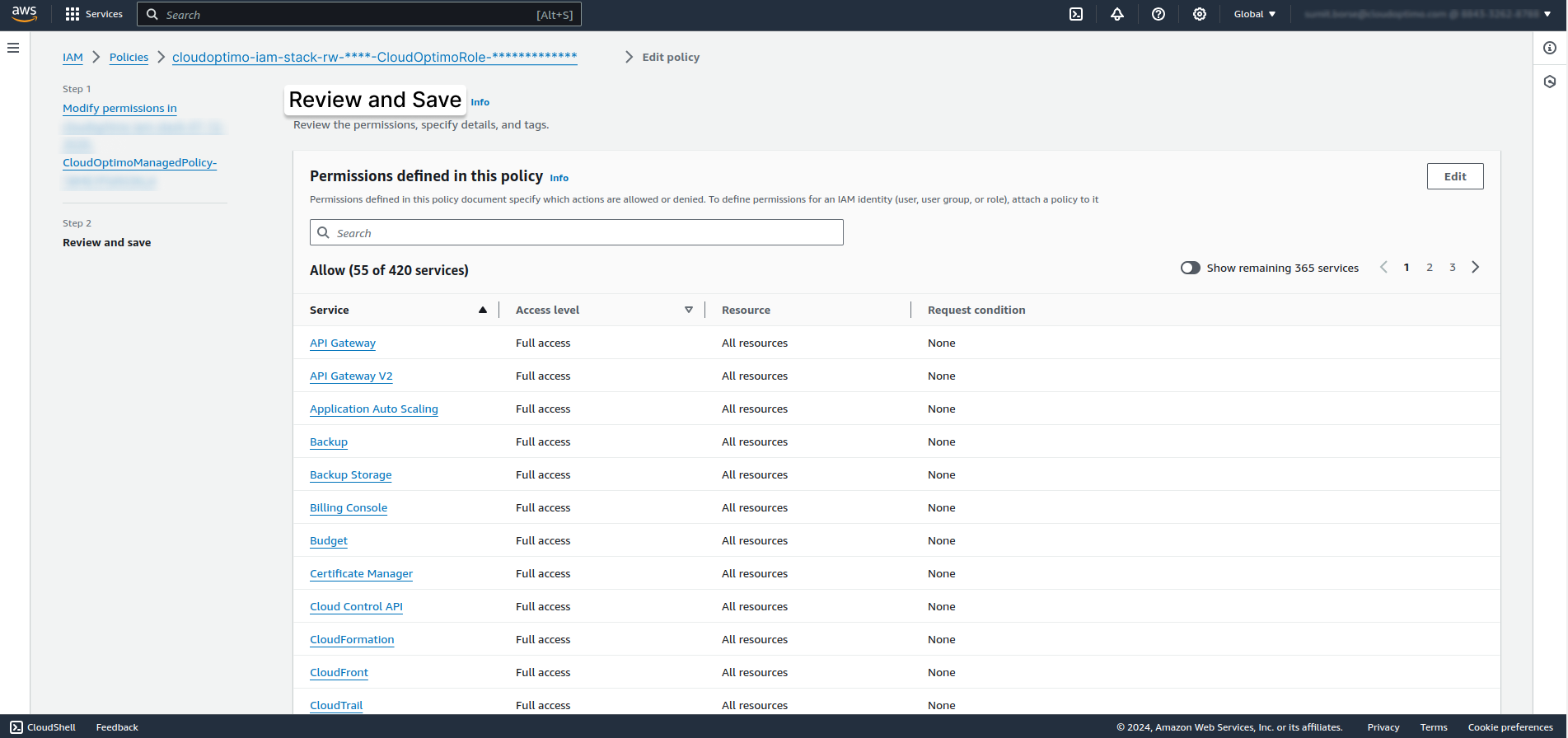
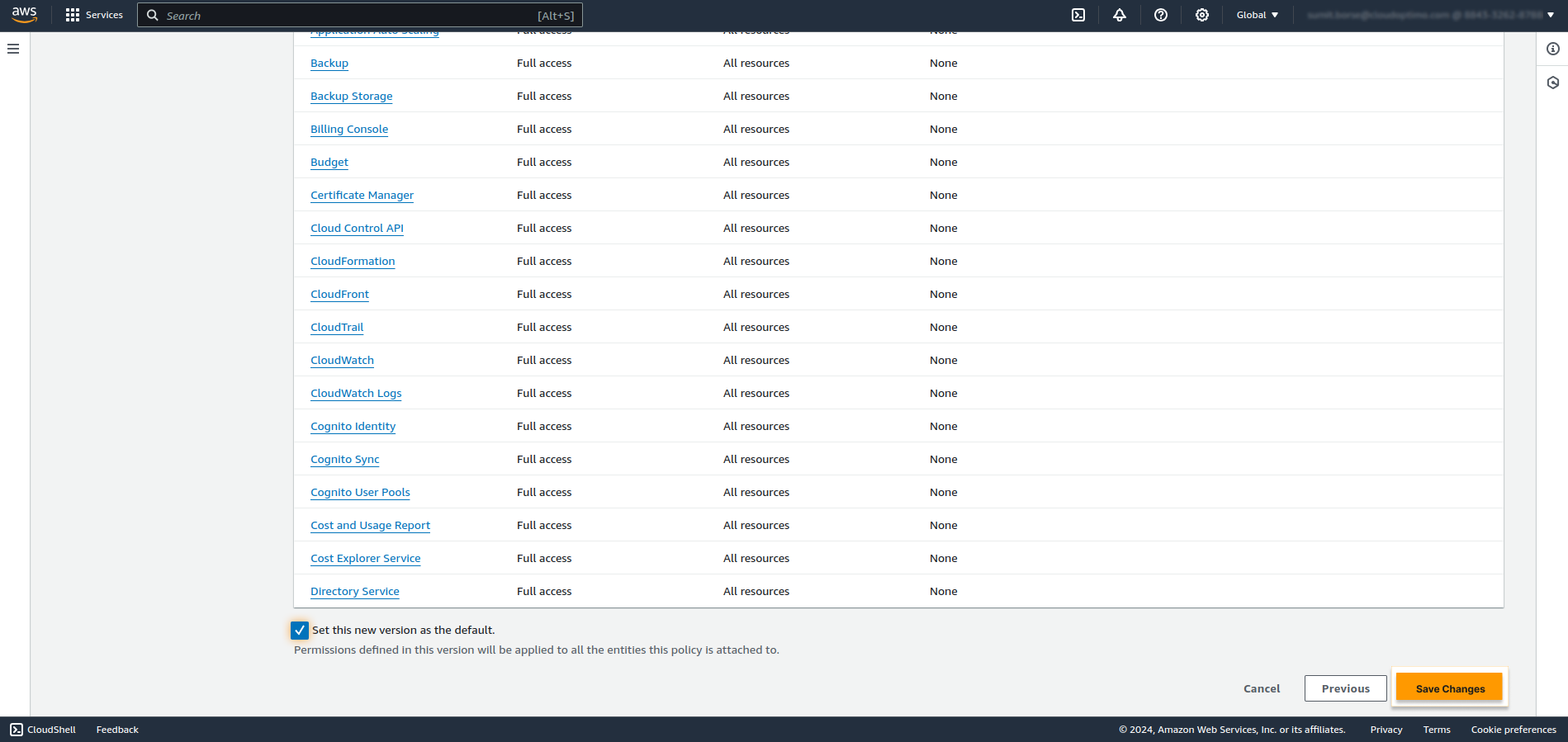
- Click on Save Changes Button
# What is the principle behind updating existing IAM policies?
- Assess how well the updated IAM policy facilitates access to the necessary data for analysis.
- Ensure that the policy provides appropriate permissions to access all relevant data sources required for analysis..
- Verify that the updated policy aligns with regulatory requirements and organizational policies governing data access and usage.
- Evaluate the security implications of the updated policy to mitigate risks associated with unauthorized data access or breaches.
